[German]On April 8/9, 2025, Microsoft rolled out numerous security updates for the supported Windows versions, which were also intended to close the symlink vulnerability CVE-2025-21204. This made waves due to the Inetpub folder being patched on all Windows systems. It is now known that the security updates have opened up a new vulnerability. Every local user can permanently prevent the update installation.
[German]On April 8/9, 2025, Microsoft rolled out numerous security updates for the supported Windows versions, which were also intended to close the symlink vulnerability CVE-2025-21204. This made waves due to the Inetpub folder being patched on all Windows systems. It is now known that the security updates have opened up a new vulnerability. Every local user can permanently prevent the update installation.
April 2025 updates and the Inetpub folder
The security updates for Windows were released on April 8, 2025 (and for some Windows versions on April 9, 2025). These close various vulnerabilities (see also Microsoft Security Update Summary (April 8, 2025)).
Among other things, the Windows symlink vulnerability CVE-2025–21204 has been patched. Improper link resolution before file access ("link following") in the Windows Update Stack allowed an authorized attacker to escalate his rights locally, according to Microsoft. The vulnerability has been rated as "Important" with a CVSS 3.1 score of 7.8.
The support article on the vulnerability CVE-2025–21204states that a new folder %systemdrive%\inetpub is created after installing the April 2025 update under Windows. This folder should not be deleted, regardless of whether Internet Information Services (IIS) is active on the target device, Microsoft wrote. This is because this behavior is part of the changes intended to increase the protection of Windows. No action is required from IT administrators or end users, it said. I reported on this in the blog post Windows 10/11: April 2025 updates create "inetpub" folder.
New vulnerability created by patches?
The patching of the Symlink vulnerabilitye CVE-2025–21204 in April 2025 by Microsoft's security updates has probably backfired. Security researcher Kevin Beaumont points out in the following BlueSky post that Microsoft's fix for a Symlink vulnerability opens up another Symlink vulnerability.
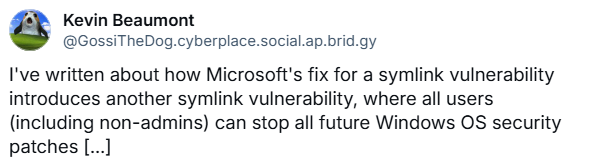
The new vulnerability allows all users (including non-administrators) to stop all future Windows security patches. Beaumont has disclosed the details in his post Microsoft's patch for CVE-2025–21204 symlink vulnerability introduces another symlink vulnerability on DoublePulsar (Martin noticed it here).
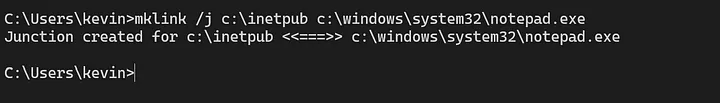
Any user (administrator or standard user) can use the mklink command in a command prompt with the command:
mklink /j c:\inetpub c:\windows\system32\notepad.exe
to create a new symlink (junction point) from the %systemdrive%\inetpub folder to another resource. Beaumont has demonstrated this in the screenshot above with a symlink to the Windows Editor Notepad.exe.
If the junction point is created on %systemdrive%\inetpub, the Windows update from April 2025 can no longer be installed, according to Beaumont. An error occurs during the update installation and/or the installation is rolled back.
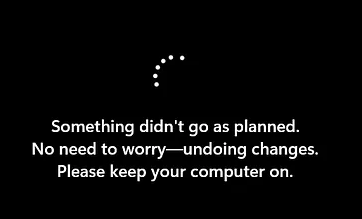
This update blockade will also apply to all future updates unless Microsoft makes improvements. Beaumont notified Microsoft of the problem two weeks ago, but has not yet received a response.
Addendum: I have tested it in a VM with Windows 10 22H2. If the April 2025 security update is installed and the inetpub folder is present, no junction can be created.
Similar articles:
Microsoft Security Update Summary (April 8, 2025)
Patchday: Windows 10/11 Updates (April 8, 2025)
Patchday: Windows Server-Updates (April 8, 2025)
Patchday: Microsoft Office Updates (April 8, 2025)
Word/Excel 2016 crashing after April 2025 update KB5002700
Outlook 2016: Calendar access blocked after April 2025 update KB5002700
Windows 10/11: April 2025 updates create "inetpub" folder
Windows NTLM vulnerability CVE-2025-24054 is being exploited